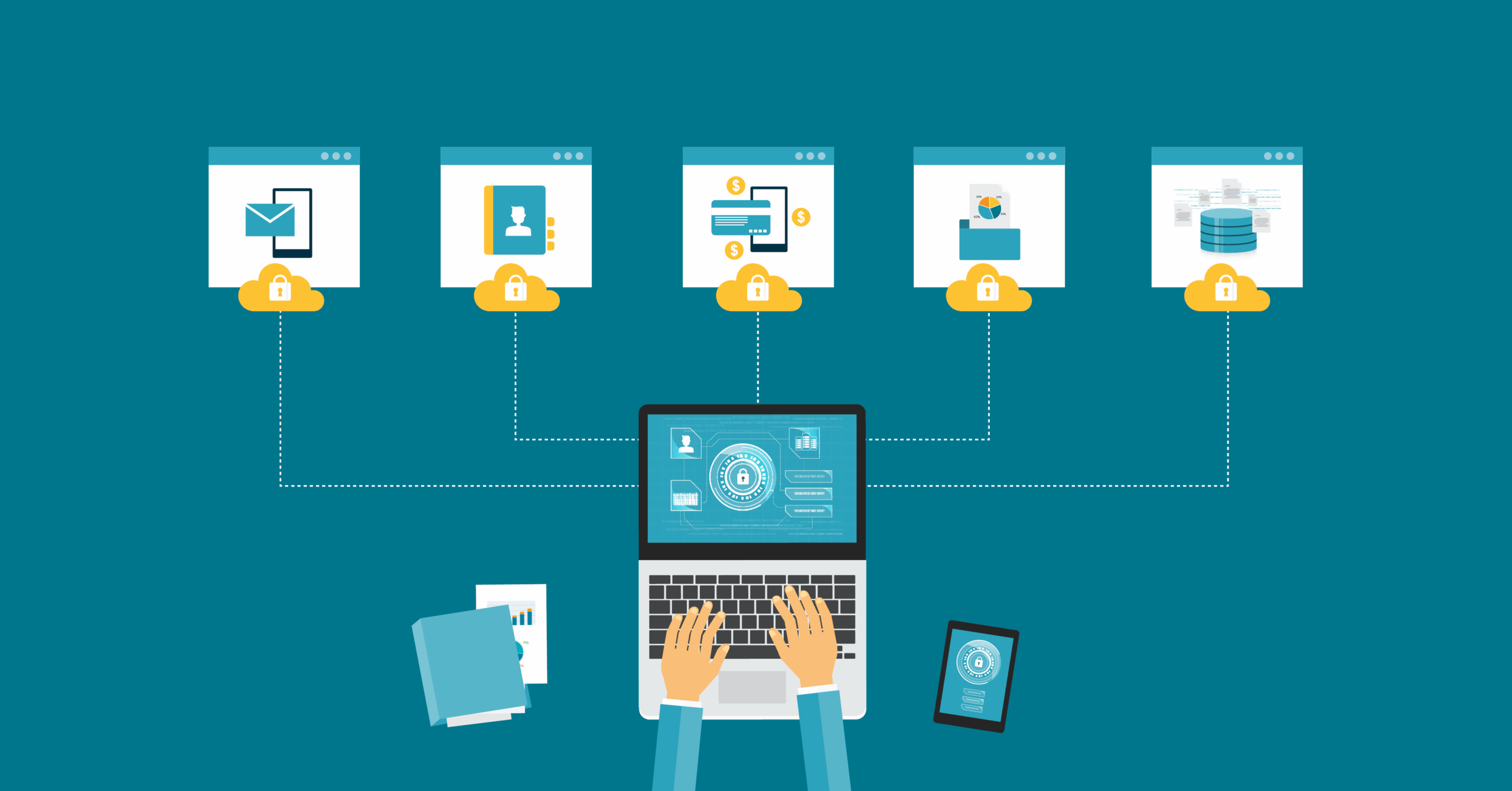
In a world increasingly driven by digital connectivity, the concept of data security often feels like navigating a labyrinth. Each turn offers concealed perils and unexpected revelations. Among these revelations, the notion of “reset encrypted data” emerges as a tantalizing enigma, akin to a phoenix rising from the ashes of potential obsolescence. This article endeavors to unravel this complex concept within the realm of device security, translating technical jargon into an engaging narrative that demystifies the intricacies involved.
The term “reset encrypted data” insinuates a process whereby previously secured information is refreshed—a kind of digital rebirth. To understand its significance, one must first appreciate the foundational role of encryption in safeguarding sensitive data. Encryption acts as the gatekeeper, transforming plain text into an indecipherable format for unauthorized eyes. This fortress of secrecy shields personal information, financial records, and private communications from lurking cyber adversaries. But what happens when a reset is warranted?
Imagine, if you will, a home whose doors are fortified with the strongest locks available. Over time, however, these once-impenetrable barriers may rust or lose their integrity due to the wear and tear of usage. The reset of encrypted data can be likened to changing the locks of this home, ensuring new safeguards are established to protect against emerging threats. This analogy encapsulates the essence of refreshing security measures in our digital habitats.
As digital devices evolve, so do the methodologies deployed by malevolent entities intent on breaching security protocols. The concept of “reset encrypted data” is particularly crucial when navigating the dual worlds of personal devices and cloud storage. Users may need to initiate a reset following device updates, changes in ownership, or potential security breaches, thereby ensuring that the encryption keys—an essential element in the defense mechanism—are altered.
When a reset occurs, the previous encryption keys become obsolete. The new keys forge a fresh path through which data traverses, creating a robust layer of protection against interception. This process is not just a procedural flush of information; it’s a digital metamorphosis. Every reset carries with it not just the potential for renewed security but also the promise of regaining control over privacy.
Operating systems and applications, be it on smartphones, tablets, or computers, often incorporate features that facilitate the reset of encrypted data. For instance, a user might find themselves prompted to reset their device following repeated unsuccessful login attempts. Here, the system is not merely reacting to security threats but is proactively adjusting the encryption framework, much like a skilled architect who reinforces a building’s foundation in response to shifting tectonic plates. This adaptability is what makes today’s device security both resilient and innovative.
However, the task of resetting encrypted data is not without its complications. The nuances can be perplexing, as users may find themselves caught in a web of notifications and configurations. It is critical to differentiate between a factory reset, which purges all information and reinstalls the operating system, and a mere reset of encrypted data, which preserves the user’s experience while enhancing security. Understanding these distinctions becomes paramount in maintaining data integrity.
Moreover, while resetting encrypted data can be illustrative of tight security measures, it also raises questions about accessibility. In instances where a reset fails or is improperly executed, users may find themselves locked out of their own data, their digital lives encapsulated in an impenetrable vault. Thus, it is vital to approach the reset procedure with a meticulous mindset—backing up essential data beforehand becomes not just prudent but a necessary step. Think of it as safeguarding valuables before embarking on an extensive renovation of one’s abode.
The significance of education in this domain cannot be understated. As users become more enlightened about the processes of reset encrypted data, they cultivate a proactive stance towards their digital security. Workshops, online tutorials, and resource-rich manuals can illuminate the pathways of encryption, ensuring individuals are prepared to take actionable steps to safeguard their information. Like the craftsman who knows the ins and outs of his tools, educated users can confidently navigate the intricacies of data security.
In many industries—finance, healthcare, and technology—the implications of improperly managed data are severe. Breaches can lead to catastrophic financial ramifications, loss of trust, and even legal consequences. The reset of encrypted data acts as a shield, a final bastion against these potential threats. It is a potent reminder that in the realm of digital security, vigilance is not merely an option; it is an obligation.
The discussion of what reset encrypted data means inevitably leads to considerations of the future. As artificial intelligence and machine learning evolve, new methods for encryption and data protection will emerge, creating a dynamic landscape that thrives on adaptability. In this ever-shifting paradigm, the ability to reset, refresh, and re-establish safeguards will determine the resilience of our digital lives.
In conclusion, the act of resetting encrypted data embodies a vital process in the narrative of device security. It symbolizes vigilance in the face of persistent threats and underscores the duty of every digital citizen to embrace best practices in securing their information. Each reset paves the way for an unwavering commitment to protection, ensuring the sanctity of our digital realms remains intact in the labyrinth of cyberspace.